Ethereum bots are burning over 50% of gas fees so ETH now needs privacy just to scale

On some Ethereum L2s, bots now burn over half the gas just searching for MEV, and they don’t pay proportionally for it. That’s a scaling and market-fairness problem rooted in market structure.
The privacy conversation in crypto has finally escaped the “anonymous money” framing that dominated the last cycle. In early 2026, the urgency is economic, not ideological.
The industry is confronting a structural problem: on-chain transparency creates extractable value at massive scale, and that extraction is now large enough to be a scaling bottleneck, not just a philosophical complaint.
Flashbots has documented how MEV-related “search spam” can consume more than 50% of gas on major layer 2s while paying a small share of fees. Alchemy, citing EigenPhi data, points to nearly $24 million in MEV profit extracted on Ethereum over just 30 days, from Dec. 8, 2025, to Jan. 6, 2026.
When a hedge fund’s $10 million DEX swap is visible in the mempool before it lands, slippage from sandwich attacks can dwarf gas costs.
Privacy is no longer a feature request. It’s a market fairness problem.
Reads, writes, proving
The Ethereum Foundation’s Privacy and Scaling Explorations team has standardized a three-part framework: private writes, private reads, and private proving.
Private reads relate to hiding transaction intent before execution. Private reads hide which users and apps are querying, such as balances and positions. Private proving is about making zero-knowledge proofs and attestations cheap and portable enough to embed everywhere.
Cais Manai, co-founder and CPO of TEN Protocol, argues the most urgent problem is reads. He stated that the industry has spent years obsessing over hiding who sent what to whom, the ‘write’ side of privacy.
However, he noted:
“The real hemorrhage right now is on the read side: the fact that every balance, every position, every liquidation threshold, every strategy is sitting there in plaintext for anyone to inspect. That’s what powers MEV. That’s what makes institutional DeFi a non-starter.”
Over 112,000 ETH, roughly $400 million at current prices, has been extracted from users by sequencers and MEV bots feeding on the readable state, according to TEN’s estimates.
The solution Manai advocates involves encrypting the entire execution environment using Trusted Execution Environments (TEEs). He explained:
“Contract state and logic stay encrypted while in use, not just at rest. Nobody reads what they’re not supposed to, because there’s nothing exposed to read.”
Tanisha Katara, founder of Katara Consulting Group, sees “writes” as the most costly problem right now.
According to her:
“Read privacy (RPC leakage, query patterns) is a slow-burning surveillance issue. Write privacy (front-running, sandwich attacks on institutional flows) is actively destroying value today. It’s hundreds of millions per year being extracted from users because their transaction intent is visible before execution. “
Andy Guzman, who leads the Ethereum Foundation’s Privacy and Scaling Explorations team, emphasizes that private reads are not widely understood.
He elaborated further:
“Private Writes is the one that currently takes most attention, it’s the ‘first base’ and arguably the first thing you have to do. Private Proving is the enabler of the other two, and it has advanced significantly in recent years. Still a lot to do.”
Private writes as the wedge
Private orderflow is a product, not research.
Flashbots’ MEV-Share operates as an order-flow auction in which users and wallets selectively share transaction data to redistribute MEV. By default, 90% of extracted value flows back to users rather than disappearing to bots.
Encrypted mempools represent the next layer. Shutter’s research documents a pathway that uses threshold encryption and timed key release, integrated with proposer-builder separation.
Transactions enter the mempool encrypted and are decrypted only after the order is committed, eliminating the public mempool as an attack surface. The design acknowledges practical constraints: latency overhead, reorg edge cases, and coordination challenges across validator sets.
The economic pressure is real enough that major infrastructure providers are building MEV protection into default flows.
Alchemy’s MEV overview characterizes the problem as systemic, with documented profit extraction totaling approximately $1 billion annually across major chains.
| Layer | What’s exposed today | Economic harm | What’s deploying now (examples) | Main bottleneck |
|---|---|---|---|---|
| Writes | Trade intent pre-execution | Sandwiching / slippage | MEV-Share, private orderflow, encrypted mempool research | Coordination + wallet defaults |
| Reads | Balances / positions / queries | Strategy leakage / MEV fuel | Private RPC, stealth addresses (ERC-5564), TEEs / confidential execution | UX + developer UX |
| Proving | Privacy proofs portability/cost | Deployment friction | zk tooling improving (Ethproofs: ~5× latency ↓, ~15× cost ↓) | Integration + product decisions |
Silent leak becoming the next headline
The Ethereum privacy roadmap now explicitly elevates private reads as a first-class track.
RPC privacy, which hides which addresses query which contracts, is important because query patterns expose strategies. If a bot observes that a specific address repeatedly checks a liquidation threshold, it knows the position is near collapse.
Wallet-side privacy primitives are where this gets practical. Stealth addresses are formally standardized under ERC-5564, enabling recipient privacy by generating unique, unlinkable addresses for each payment.
The specification exists, but broad wallet adoption remains hindered by UX challenges, including scanning incoming payments, reconciling balances across ephemeral addresses, and the complexity of key management.
Manai’s developer UX argument hits hardest here:
“The real UX bottleneck in 2026 is developer UX, the gap between ‘I want to build a private application’ and actually being able to do it without learning an entirely new programming model, a custom language, or a bespoke proving system.”
He highlighted the need for full EVM/SVMs running within TEEs so developers can build encrypted dApps using the same tools, languages, and mental models they already have. No circuits to write, no custom VMs to learn.
Proving is improving fast enough
Zero-knowledge proving costs have collapsed. Ethproofs’ 2025 review documents onboarding multiple zkVMs and provers, verifying roughly 200,000 blocks, and seeing latency fall approximately fivefold while costs dropped around fifteenfold over the year.
Proof generation is no longer the primary constraint on privacy deployment.
The bottleneck has shifted to coordination and integration. Guzman identifies user experience and cost as the primary barriers for retail users, and regulation and compliance as the primary barriers for institutions.
He said:
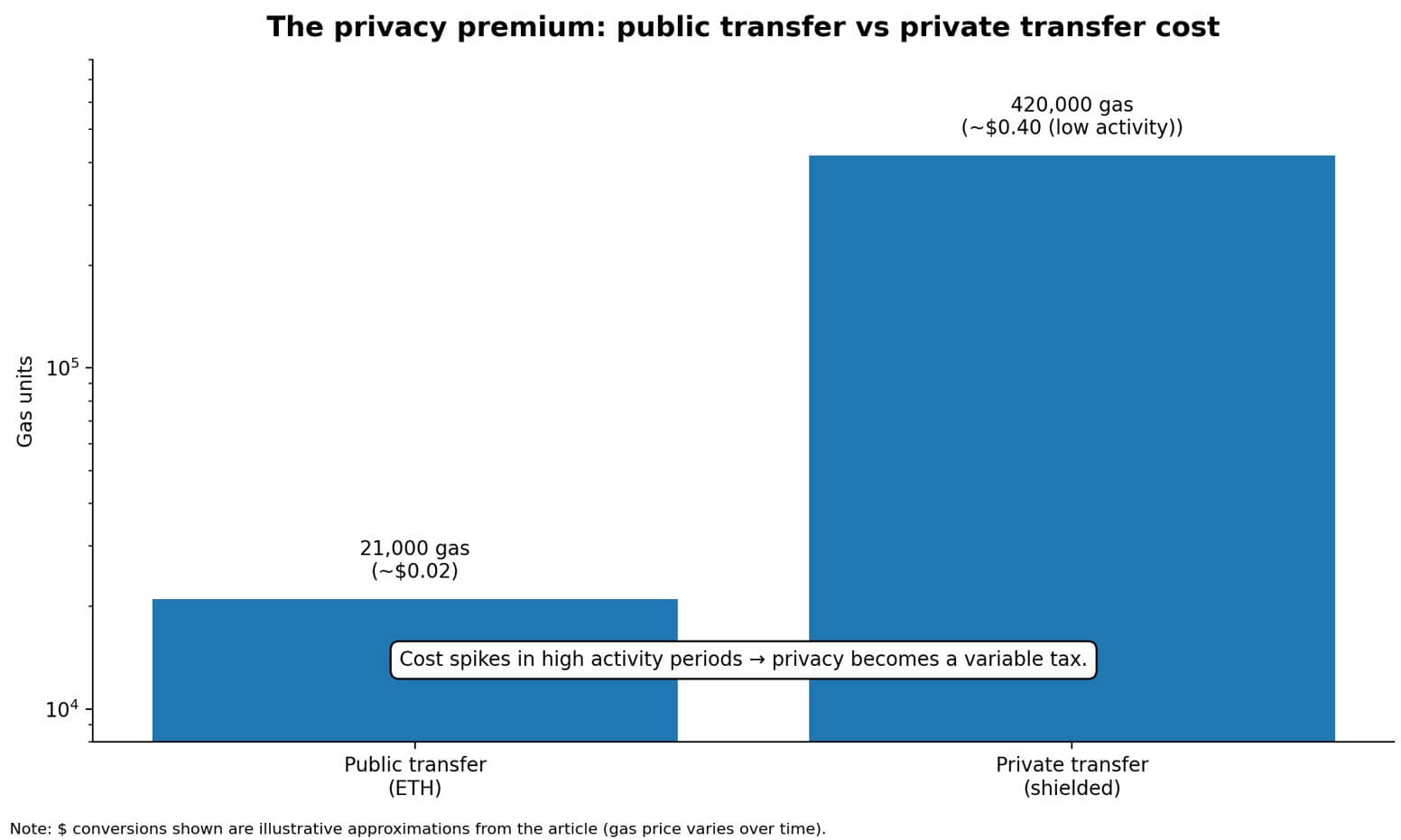
“The cheapest transaction you can send on Ethereum is around 21,000 gas, roughly $0.02. A private transfer can easily be 420,000 gas or more. In periods of low activity, it’s okay (around $0.40), but high activity could become costly for some use cases.”
Katara frames it as a coordination problem:
“Proof cost was the bottleneck in 2023-24. It’s resolving. The coordination problem is the bottleneck: Who decides that shielded sends are on by default in a wallet? Who governs the key server threshold in an encrypted mempool? These are the unsexy mechanism design problems that determine whether privacy actually reaches users.”
Regulation is shaping the design space, not blocking it
Privacy builders are designing in the shadow of compliance requirements and legal risk.
The US Treasury delisted Tornado Cash sanctions in 2025, but legal uncertainty didn’t vanish. Tornado Cash developer Roman Storm faced a mixed verdict: guilty on an unlicensed money-transmitting business charge, with the jury deadlocked or acquitted on other counts.
On the compliance side, the EU’s crypto travel rule regime under Regulation (EU) 2023/1113 took effect on Dec. 30, 2024, requiring the collection and transmission of identities for crypto-asset transfers.
Privacy isn’t disappearing, but being productized into forms that can survive regulation: selective disclosure, policy controls, auditability windows.
Permanent opacity scares regulators. Privacy that’s auditable on a schedule is something they can work with.
Katara notes the irony:
“Permissioned and enterprise chains may deliver default privacy to institutional users before public chains deliver it to retail.”
What minimum viable privacy looks like in 2026
For the average MetaMask user in 2026, Katara expects one-address-per-application to become more common, optional shielded sends in a few wallets, and early RPC privacy features.
Guzman points to stealth addresses and shielded pools as already practical, with UI improving rapidly:
“I think we are going to see more L2s specializing in payments and private transfers.”
Manai is more pessimistic about defaults on most chains. He stated:
“Honestly? Close to nothing. The average user in 2026 is still broadcasting every swap, every balance check, every approval in plaintext. The minimum viable privacy should be: your balances aren’t public, your trade intent isn’t visible before execution, and you’re not losing value to front-runners.”
Three paths forward
The first scenario is that MEV makes privacy unavoidable.
Wallets and apps continue to integrate private transaction pathways, such as private RPC, MEV-Share-style routing, and per-app addressing. The trigger is sustained MEV extraction plus more institutional capital moving on-chain.
The second scenario is confidential execution goes enterprise-first. TEEs and policy-based encryption gain traction in controlled environments, such as institutions, regulated apps, and private markets, because they prioritize business confidentiality over consumer anonymity.
The third scenario is that regulatory chill pushes privacy to an opt-in-only model. If enforcement focuses broadly on privacy tooling, retail privacy UX stays niche. Teams shift to selective disclosure and “policy privacy” designs, such as Privacy Pools, rather than generalized shielding.
Privacy in 2026 isn’t a feature. It’s a response to structural problems that became too expensive to ignore.
MEV extraction, strategy leakage, and on-chain surveillance create quantifiable losses at an institutional scale. The technology to address those problems exists: encrypted mempools, stealth addresses, confidential execution environments, and zero-knowledge proving with collapsed costs.
The barrier isn’t cryptography anymore. It’s coordination, developer UX, and the unsexy work of making privacy the default rather than opt-in.
The industry spent the last cycle building privacy as an exception. The next cycle will determine whether privacy becomes infrastructure (boring, invisible, and everywhere) or remains a niche feature for the paranoid and the institutional.
The difference comes down to whether the people building wallets, apps, and protocols decide that leaking everything by default is a bug worth fixing. In 2026, the economists finally suggest it’s a bug.