Decentralized finance (DeFi) lending platform Venus Protocol has helped a consumer recuperate stolen crypto following a phishing assault tied to North Korea’s Lazarus Group.
On Thursday, Venus Protocol introduced that it had efficiently helped a consumer recuperate $13.5 million in crypto after the phishing incident that occurred on Tuesday. On the time, Venus Protocol paused the platform as a precautionary measure and began investigating.
In response to Venus, the pause halted additional fund motion, whereas audits confirmed Venus’ sensible contracts and entrance finish had been uncompromised.
Emergency vote permits fund restoration
An emergency governance vote allowed the compelled liquidation of the attacker’s pockets, enabling stolen tokens to be seized and despatched to a restoration handle.
Attackers exploited a malicious Zoom shopper
Within the autopsy, Venus revealed that the attackers used a malicious Zoom shopper to trick the sufferer into granting delegated management over the account.
This allowed the perpetrators to borrow and redeem on the sufferer’s behalf, enabling them to empty hundreds of thousands in stablecoins and wrapped property.
Nonetheless, the protocol’s safety companions HExagate and Hypernative flagged the suspicious transaction inside minutes, resulting in the choice to pause the protocol. In response to Venus, the restoration course of unfolded in lower than 12 hours.
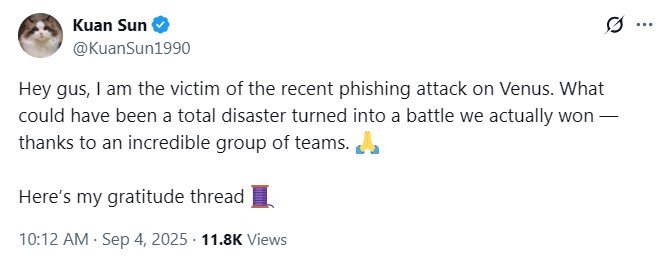
Kuan Solar, who was recognized because the sufferer of the assault, thanked the groups behind the restoration. “What may have been a complete catastrophe was a battle we truly received, because of an unbelievable group of groups,” Solar wrote.
Safety companions HExagate and Hypernative flagged the suspicious exercise inside minutes, prompting the pause. PeckShield, Binance, and SlowMist later assisted within the restoration.
Associated: WLFI blocks hacking makes an attempt with onchain blacklisting
Phishing assault linked to the Lazarus Group
SlowMist’s evaluation linked the assault to the Lazarus Group, a North Korea-backed collective blamed for main crypto heists, together with the $600M Ronin bridge exploit and the $1.5B Bybit hack.
Solar mentioned SlowMist carried out intensive evaluation work and “had been among the many very first to level out that Lazarus was behind this assault.”
The Lazarus Group is a North Korea-linked hacking collective believed to function beneath the nation’s intelligence company.
The group has been tied to a number of the greatest crypto heists in historical past, together with the $600-million Ronin bridge exploit and the $1.5 billion Bybit hack.
Journal: Astrology may make you a greater crypto dealer: It has been foretold