Menace actors have discovered a brand new solution to ship malicious software program, instructions, and hyperlinks inside Ethereum sensible contracts to evade safety scans as assaults utilizing code repositories evolve.
Cybersecurity researchers at digital asset compliance agency ReversingLabs have discovered new items of open-source malware found on the Node Bundle Supervisor (NPM) bundle repository, a big assortment of JavaScript packages and libraries.
The malware packages “make use of a novel and artistic approach for loading malware on compromised units – sensible contracts for the Ethereum blockchain,” ReversingLabs researcher Lucija Valentić stated in a Wednesday weblog put up.
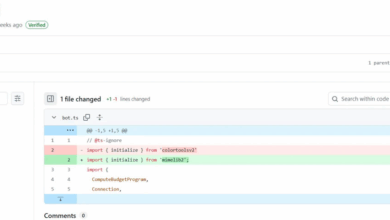
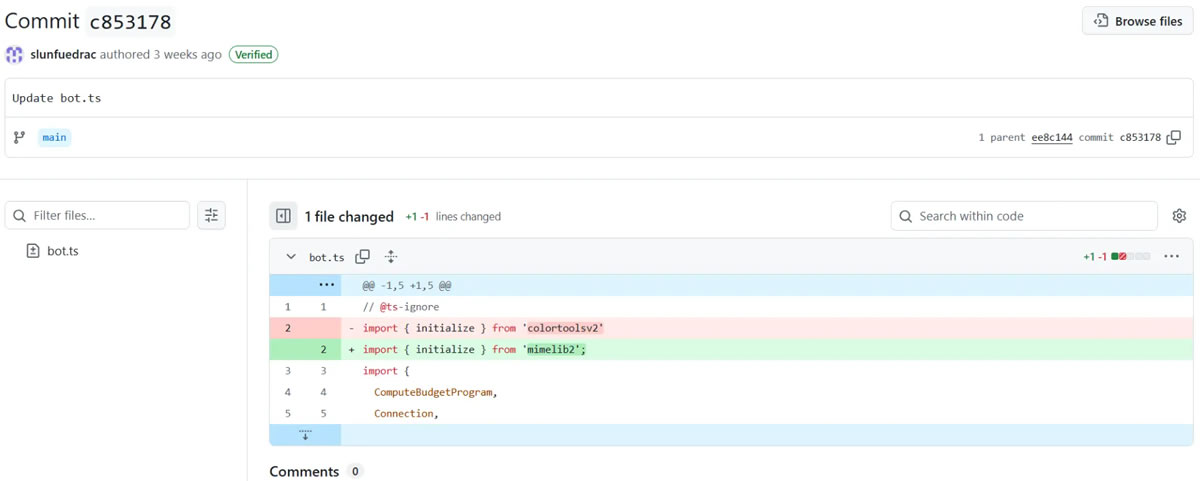
The 2 packages, ‘colortoolsv2’ and ‘mimelib2’, revealed in July, “abused sensible contracts to hide malicious instructions that put in downloader malware on compromised techniques,” defined Valentić.
To keep away from safety scans, the packages functioned as easy downloaders and as a substitute of straight internet hosting malicious hyperlinks, they retrieved command and management server addresses from the sensible contracts.
When put in, the packages would question the blockchain to fetch URLs for downloading second-stage malware, which carries the payload or motion, making detection harder since blockchain visitors seems legit.
A brand new assault vector
Malware concentrating on Ethereum sensible contracts is just not new and has been utilized by North Korean-affiliated hacking collective, the Lazarus Group, earlier this 12 months.
“What’s new and totally different is the usage of Ethereum sensible contracts to host the URLs the place malicious instructions are situated, downloading the second-stage malware,” stated Valentić, who added:
“That’s one thing we haven’t seen beforehand, and it highlights the quick evolution of detection evasion methods by malicious actors who’re trolling open supply repositories and builders.”
An elaborate crypto deception marketing campaign
The malware packages had been half of a bigger, elaborate social engineering and deception marketing campaign primarily working by means of GitHub.
Menace actors created pretend cryptocurrency buying and selling bot repositories designed to look extremely reliable by means of fabricated commits, pretend consumer accounts created particularly to observe repositories, a number of maintainer accounts to simulate energetic growth, and professional-looking venture descriptions and documentation.
Associated: Crypto customers warned as adverts push malware-laden crypto apps
Menace actors are evolving
In 2024, safety researchers documented 23 crypto-related malicious campaigns on open-source repositories, however this newest assault vector “exhibits that assaults on repositories are evolving,” combining blockchain know-how with elaborate social engineering to bypass conventional detection strategies, Valentić concluded.
These assaults will not be solely executed on Ethereum. In April, a pretend GitHub repository posing as a Solana buying and selling bot was used to distribute obscured malware that stole crypto pockets credentials. Hackers have additionally focused ‘Bitcoinlib’, an open-source Python library designed to make Bitcoin growth simpler.
Journal: Bitcoin to see ‘yet one more huge thrust’ to $150K, ETH strain builds: Commerce Secrets and techniques