The 2025 Favrr heist
In a twist worthy of a cyber‑thriller, a gaggle posing as blockchain builders pulled off a $680,000 heist on fan token market Favrr in June 2025, solely to be unmasked when one in every of their very own gadgets was counter‑hacked.
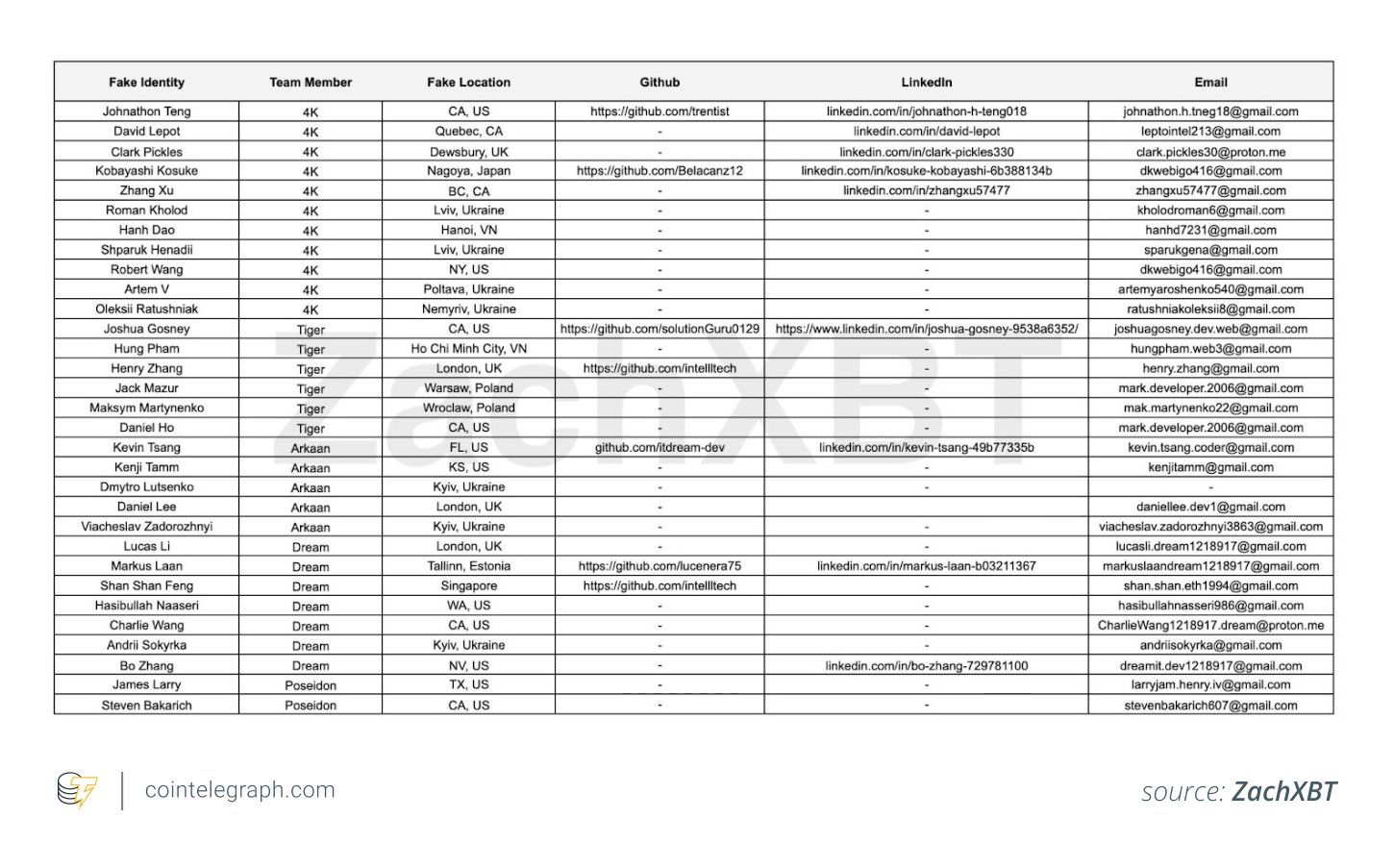
What emerged was startling: Six North Korean operatives had no less than 31 faux identities. They carried cast authorities IDs, cellphone numbers and fabricated LinkedIn and Upwork profiles. Some even posed as expertise from Polygon Labs, OpenSea and Chainlink to infiltrate the crypto business.
The digital breadcrumbs (screenshots, Google Drive exports, Chrome profiles) revealed simply how meticulously they orchestrated the infiltration.
Crypto investigator ZachXBT traced their exercise onchain, connecting one pockets deal with to the Favrr exploit and confirming this was not only a phishing scheme however a coordinated developer‑degree infiltration.
Do you know? North Korea-linked hackers stole about $1.34 billion in crypto in 2024, accounting for 60% of worldwide thefts. The assaults spanned 47 incidents, double the quantity from the earlier 12 months.
How the hack was found
The Favrr breach got here to gentle by a twist of cyber destiny — one of many alleged North Korean operators was counter-hacked.
An unnamed supply gained entry to one in every of their gadgets, unveiling a trove of inside artifacts: screenshots, Google Drive exports and Chrome profiles that mapped out how the hackers coordinated their scheme
These information painted a startling image: six operatives operating no less than 31 faux identities.
Their operational playbook was revealed intimately, from spreadsheets that tracked bills and deadlines to Google Translate facilitating their English-language deception, proper right down to rented computer systems, VPNs and AnyDesk for stealthy entry.
Crypto sleuth ZachXBT then traced the stolen funds onchain, uncovering a pockets deal with “intently tied” to the $680,000 Favrr exploit in June 2025.
Collectively, these revelations verify this was a deeply coordinated infiltration by expert actors posing as professional builders, all uncovered by a tool left weak.
The faux developer scheme
The counter-hack revealed an arsenal of fabricated personas that went far past mere usernames.
They acquired government-issued IDs, cellphone numbers and even bought LinkedIn and Upwork accounts, enabling them to convincingly current themselves as skilled blockchain builders.
Some even impersonated employees from high-profile entities, interviewing as full-stack engineers for Polygon Labs and boasting expertise with OpenSea and Chainlink.
The group maintained pre‑written interview scripts, sharpening scripted responses tailor-made to every faux identification.
In the end, this layered phantasm allowed them to land developer roles and entry delicate techniques and wallets, performing from the within whereas hiding behind expertly crafted avatars.
This was deep, identity-based infiltration.
The instruments and ways they used
The ingenuity of North Korean hacking right here lay in meticulously orchestrated deception utilizing on a regular basis instruments.
Coordination among the many six operatives was dealt with through Google Drive exports, Chrome profiles and shared spreadsheets that mapped duties, scheduling and budgets — all meticulously logged in English and smoothed over with Google Translate between Korean and English.
To execute their infiltration with precision, the staff relied on AnyDesk distant entry and VPNs, masking their true places whereas showing as professional builders to unsuspecting employers. In some circumstances, they even rented computer systems to additional obfuscate their origin.
Leaked monetary paperwork revealed that their operations have been closely budgeted. In Could 2025, the group spent $1,489.80 on operational bills, together with VPN subscriptions, rented {hardware} and infrastructure wanted for sustaining a number of identities.
Behind the guise {of professional} collaboration lay a fastidiously engineered phantasm, a corporate-like undertaking administration system supporting deep intrusions, backed by real-world operational expenditures and technological cowl.
Do you know? North Korea’s most superior cyber unit, Bureau 121, is staffed by a few of the regime’s prime technical expertise, many handpicked from elite universities after an intensive multi-year coaching course of.
Distant job infiltration
The North Korean group behind the Favrr heist used seemingly professional job functions (as a substitute of spam or phishing, surprisingly).
Working by Upwork, LinkedIn and different freelance platforms, they secured blockchain developer roles. With polished personas, full with tailor-made resumes and interview-ready scripts, they gained entry to consumer techniques and wallets beneath the guise of distant employment. The infiltration was so genuine that some interviewers doubtless by no means suspected something was amiss.
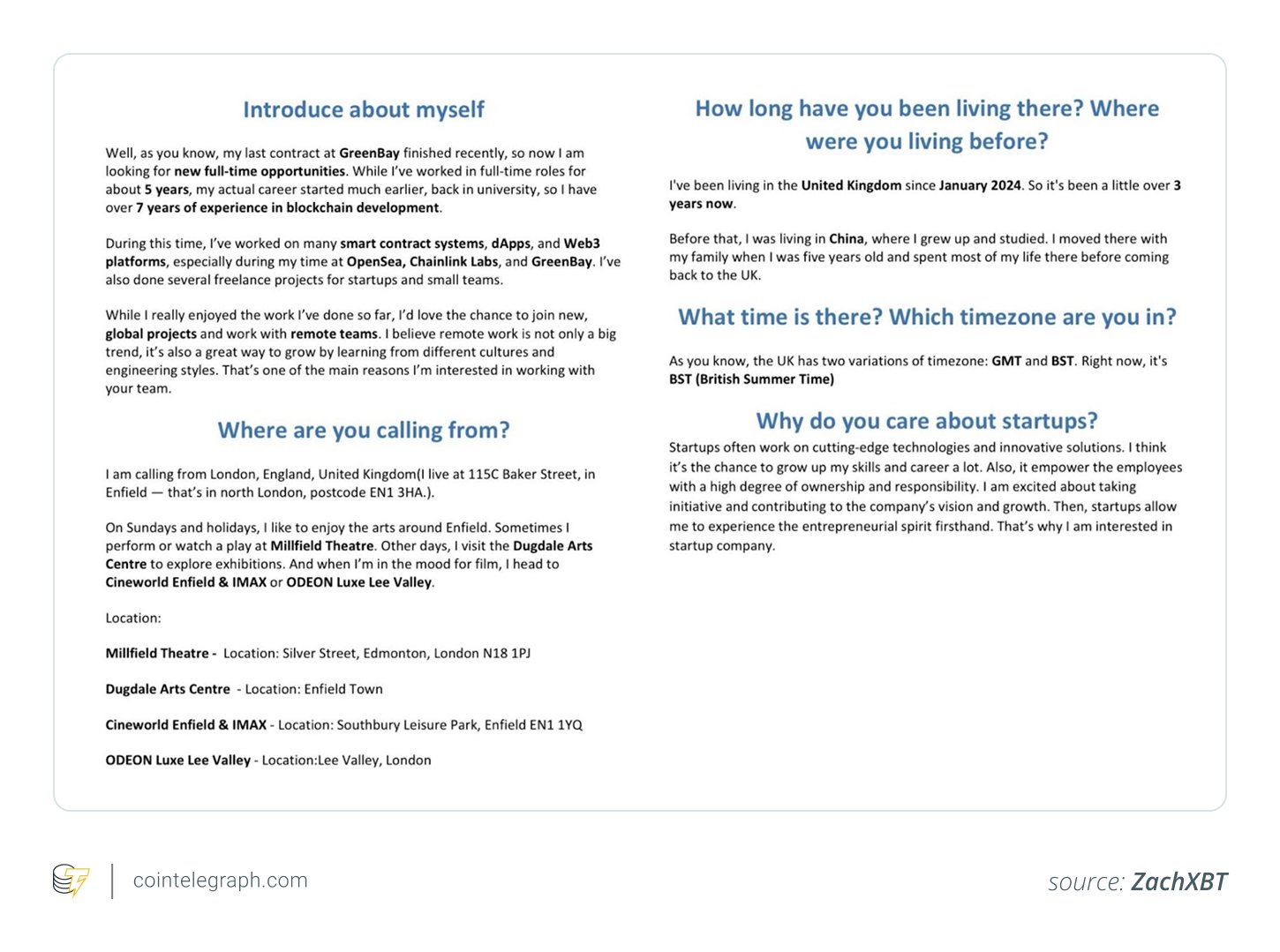
This tactic is consultant of one thing larger. Investigations reveal a broader, well-established sample: North Korean IT operatives routinely infiltrate organizations by securing distant positions. These infiltrators cross background and reference checks utilizing deepfake instruments and AI-enhanced resumes, delivering companies whereas paving the way in which for malicious exercise.
In essence, the cyber-espionage risk isn’t restricted to malware. This occasion reveals that it’s additionally embedded inside trusted entry by distant work infrastructure.
Do you know? By 2024, North Korea had round 8,400 cyber operatives embedded worldwide, posing as distant staff to infiltrate firms and generate illicit income, notably channeling funds towards the regime’s weapons packages.
Broader context and state-backed ops
In February 2025, North Korea’s Lazarus Group (working beneath the alias TraderTraitor) executed the biggest cryptocurrency heist thus far, stealing roughly $1.5 billion in Ether from the Bybit trade throughout a routine pockets switch.
The US Federal Bureau of Investigation confirmed the hack and warned the crypto business to dam suspicious addresses, noting this assault as a part of North Korea’s broader cybercrime technique to fund its regime, together with nuclear and missile packages.
Past huge direct thefts, North Korea has additionally leveraged extra covert means. Cybersecurity researchers, together with Silent Push, found that Lazarus associates arrange US shell firms, Blocknovas and Softglide, to distribute malware to unsuspecting crypto builders by faux job gives.
These campaigns contaminated targets with strains like BeaverTail, InvisibleFerret and OtterCookie, granting distant entry and enabling credential theft.
These methods reveal a twin risk: brazen exchange-level assaults and stealthy insider infiltration. The overarching objective stays constant: to generate illicit income beneath the radar of sanctions.
It’s value remembering that such cybercrime operations are central to funding North Korea’s weapons packages and sustaining the regime’s foreign-currency lifeline.